Ever wondered how journalists uncover hidden connections between public figures? Or how security analysts track down cybercriminals across continents? They’re not using classified databases or government clearances. They’re leveraging publicly available information through a discipline called OSINT—and you can learn these same techniques.
The digital age has created an unprecedented information landscape. Every social media post, business registration, property record, and forum comment leaves a trail. Open Source Intelligence (OSINT) transforms these scattered digital breadcrumbs into actionable intelligence. Whether you’re a private investigator, security professional, journalist, or simply curious about digital footprints, this guide shows you exactly how it’s done.
What OSINT Actually Means (And Why It Matters Now)
OSINT stands for Open Source Intelligence—the practice of collecting and analyzing publicly accessible information from legal sources. This includes social media platforms, public records, news archives, business registrations, domain records, and countless other data points scattered across the web.
Unlike hacking or unauthorized access, OSINT operates entirely within legal boundaries. You’re not breaking into systems; you’re methodically connecting dots that anyone could theoretically find, but few have the skills to piece together.
The explosion of digital data has made OSINT increasingly powerful. In 2020, researchers estimated that 90% of the world’s data was created in just the previous two years. This information tsunami means more traces, more connections, and more opportunities for those who know where to look.
The OSINT Investigation Framework: Five Critical Phases
Professional OSINT investigations follow a structured approach. Here’s the framework used by intelligence analysts worldwide:
Phase 1: Define Your Requirements
Start with crystal-clear objectives. Poor investigations begin with vague goals like “find everything about this person.” Effective investigations define specific intelligence requirements:
- What exactly do you need to know?
- What decisions will this information support?
- What level of confidence do you need?
- What’s your deadline?
A corporate investigator might need to verify employment history for due diligence. A journalist might seek connections between political donors and policy decisions. Different goals demand different approaches.
Phase 2: Source Discovery and Collection
This phase separates novices from professionals. Beginners search Google and stop there. Skilled practitioners systematically work through multiple information layers:
Layer One: Direct Sources Target’s personal websites, blogs, social media profiles (LinkedIn, Twitter, Facebook, Instagram), professional portfolios, and published content provide firsthand information directly from the subject.
Layer Two: Public Records Business registrations, property records, court documents, permits, licenses, voter registrations, and corporate filings offer officially verified data points that subjects often forget exist.
Layer Three: Digital Residue Cached pages, deleted social media posts (recovered through archives), old forum comments, GitHub commits, and metadata in published documents reveal historical information targets may have tried to erase.
Layer Four: Secondary Sources News articles, press releases, conference attendee lists, professional association directories, and industry publications provide third-party context and verification.
Phase 3: Processing and Correlation
Raw data means nothing without context. This phase transforms isolated facts into intelligence:
Timeline Construction Plot events chronologically. When did they change jobs? When did they move cities? When did their social media activity patterns shift? Timelines reveal gaps that demand explanation.
Network Mapping Who appears repeatedly in their professional life? Their social circles? Their business dealings? Maltego and similar visualization tools help map these connections, often revealing non-obvious relationships.
Cross-Reference Verification Never trust a single source. Claims on LinkedIn should match business registrations. Social media locations should align with property records. Discrepancies signal either errors or deliberate deception.
Phase 4: Analysis and Interpretation
This separates data collectors from intelligence analysts. What do the patterns mean? Consider:
Behavioral Patterns Does the target post from specific locations? Do they maintain predictable schedules? Do they use consistent usernames across platforms? These patterns enable prediction.
Risk Assessment Red flags include discrepancies between claimed and actual credentials, associations with sanctioned entities, patterns of litigation, unexplained wealth, or systematic information scrubbing.
Confidence Levels Rate each finding: confirmed (multiple independent sources), probable (single reliable source), possible (unverified but plausible), or speculative (requires further investigation).
Phase 5: Reporting and Dissemination
Intelligence has no value if it doesn’t inform decisions. Professional reports include:
- Executive summary (key findings in 2-3 paragraphs)
- Detailed findings with source citations
- Timeline of significant events
- Network relationship map
- Confidence assessments for each claim
- Gaps and recommendations for further investigation
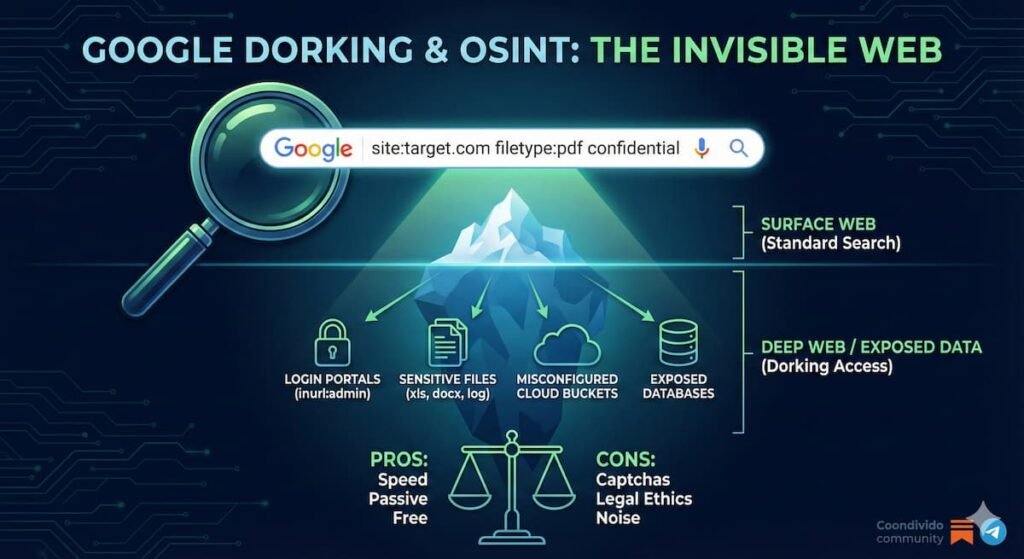
Essential OSINT Tools: The Professional Toolkit
Effective OSINT relies on the right tools. Here’s what professionals actually use:
Search and Discovery Tools
Google Dorking Advanced search operators transform Google from a simple search engine into a precision intelligence tool. Commands like site:, filetype:, inurl:, and intitle: narrow results dramatically.
Example: site:linkedin.com "cybersecurity analyst" "New York" finds LinkedIn profiles matching those criteria.
Maltego The industry standard for link analysis and network mapping. Input a name, email, or domain, and watch Maltego automatically discover connections, associated entities, and hidden relationships. The commercial version provides access to numerous transform integrations.
SpiderFoot Automated OSINT collection across 100+ data sources. Input a domain, IP address, email, or name, and SpiderFoot systematically gathers associated data points. Particularly powerful for technical investigations involving infrastructure and domain reconnaissance.
Social Media Investigation Tools
Social Searcher Real-time social media monitoring across major platforms. Track mentions, hashtags, and keywords without platform-specific APIs. Free tier allows limited searches; paid tiers unlock historical data and advanced filtering.
Twint Twitter scraping without API limitations. Extract tweets, followers, following lists, and engagement data even from protected accounts (public data only). Bypasses Twitter’s rate limiting, making it ideal for comprehensive Twitter investigations.
IntelTechniques Custom Tools Michael Bazzell’s collection of custom search tools provides pre-configured searches across dozens of platforms. Instead of manually crafting search queries, these tools provide one-click access to optimized searches for Facebook, Instagram, Reddit, TikTok, and more.
People Finding Resources
BeenVerified / Spokeo Commercial people search engines aggregating public records, social media, contact information, and background data. Paid services, but often worth the investment for U.S.-based investigations.
Pipl Deep web people search that scours databases, social networks, and online publications. Particularly effective for finding individuals with common names by correlating multiple data points.
Dehashed Searches data breach dumps for emails, usernames, passwords, and associated information. Invaluable for discovering which services a target uses and whether their credentials have been compromised.
Domain and Infrastructure Tools
Whois Lookup Reveals domain registration details, including registrant information (unless privacy-protected), name servers, registration and expiration dates, and historical ownership changes.
BuiltWith Analyzes website technology stacks. What CMS does the site use? What analytics platforms? What payment processors? This intelligence helps identify vulnerabilities and connections to other properties.
SecurityTrails Historical DNS records, subdomains, and IP history. Discover old websites, hidden subdomains, and infrastructure connections that reveal organizational relationships.
Image and Geolocation Tools
Google Reverse Image Search / TinEye Upload an image to find where else it appears online. Discover if profile photos are stock images, stolen identities, or reused across multiple accounts.
GeoSpy AI-powered geolocation that analyzes images to estimate where they were taken. Examines architectural styles, vegetation, signage, weather conditions, and other visual clues.
Jeffrey’s Image Metadata Viewer Extracts EXIF data from images, potentially revealing camera model, GPS coordinates, and timestamp—all information photographers often forget to strip before posting.
Archive and Historical Tools
Wayback Machine The Internet Archive’s massive repository of historical web pages. View how websites looked years ago, recover deleted content, and track changes over time.
Archive.today Create permanent snapshots of web pages. Unlike Wayback Machine (which crawls periodically), Archive.today captures specific pages on demand, preserving evidence before it disappears.
Cached Pages Google cache and other cached page repositories preserve recent versions of websites. Useful for recovering recently deleted content that hasn’t yet been archived.
Advanced OSINT Techniques: Beyond Basic Searches
Once you’ve mastered fundamental tools, these advanced techniques separate competent investigators from exceptional ones:
Username Enumeration
Most people reuse usernames across platforms. Find one username, and you can potentially discover their presence on dozens of services.
NameCheck / Sherlock Automated username checkers that query hundreds of platforms simultaneously. Input a username and discover every site where it’s registered.
Manual verification remains critical—automated tools generate false positives, and clever investigators manually check variations (adding numbers, underscores, or slight spelling changes).
Email Pattern Recognition
Corporate email addresses typically follow predictable patterns: firstname.lastname@company.com or flastname@company.com. Once you identify the pattern, you can predict addresses for other employees.
Hunter.io Discovers email patterns for any domain and provides confidence scores for predicted addresses. The free tier allows limited searches; paid tiers unlock bulk lookups.
Email Permutator Generates all possible email combinations for a name and domain. Pair this with email verification services to confirm which addresses actually exist.
OPSEC Failures and Digital Leakage
People underestimate their digital exposure. Common OPSEC failures include:
- Reusing usernames across personal and professional accounts
- Posting location-tagged photos revealing home or workplace addresses
- Including metadata in shared documents
- Using personal email addresses for business signups
- Maintaining old accounts with outdated information that contradicts current claims
Systematic checking of these common failures often yields breakthrough intelligence.
Blockchain Investigation
Cryptocurrency transactions leave permanent public records. While wallet addresses seem anonymous, behavioral analysis often enables de-anonymization:
- Transaction timing patterns (when does this wallet transact?)
- Transaction amounts (do they match known purchases?)
- Wallet clustering (which addresses interact frequently?)
- Exchange interactions (transactions to known exchange deposit addresses)
Chainalysis / Elliptic Commercial blockchain intelligence platforms used by law enforcement and financial institutions. Expensive, but unmatched for serious cryptocurrency investigations.
Legal and Ethical Boundaries: Staying on the Right Side
OSINT operates entirely within legal boundaries, but those boundaries matter:
What’s Legal
- Accessing publicly available websites and social media
- Searching public records databases
- Using information from data breaches (viewing, not participating in breaches)
- Creating accounts to access publicly available information
- Aggregating and analyzing public information
What’s Illegal or Unethical
- Unauthorized access to systems (hacking)
- Password cracking or exploitation
- Impersonation to gain information
- Social engineering through deception
- Harassment or stalking
- Violating terms of service in ways that constitute unauthorized access
The line between aggressive investigation and illegal activity can blur. When in doubt, consult legal counsel before proceeding.
Privacy Considerations
Just because information is technically public doesn’t mean collecting it is ethical. Consider:
- Is the subject a public figure or private individual?
- What’s the legitimate purpose of this investigation?
- Could this information cause harm if aggregated?
- Are you respecting reasonable expectations of privacy?
Professional investigators operate under codes of ethics that go beyond mere legality.
Real-World OSINT: Three Investigation Examples
Case Study 1: Corporate Due Diligence
A venture capital firm was considering a $5M investment in a startup. The CEO claimed extensive experience at major tech companies and a Stanford MBA.
Investigation Process:
- LinkedIn profile matched claimed credentials
- Stanford alumni database search found no record (red flag)
- Wayback Machine revealed the CEO’s LinkedIn previously listed a different, less prestigious university
- News archives found no mentions at the claimed companies despite supposedly senior positions
- Corporate registrations revealed the CEO’s involvement in two previous failed startups, neither mentioned in pitch materials
Outcome: Investment declined. Further investigation revealed the CEO had systematically fabricated credentials.
Case Study 2: Missing Person Located
A family sought to locate a relative who had lost contact three years earlier. Last known location was Las Vegas; last known employer had no forwarding information.
Investigation Process:
- Social media accounts last updated 2.5 years ago
- Username enumeration found active accounts on gaming forums under the same username
- Forum posts mentioned a recent move to Portland
- Property records search in Portland (using variations of the name) found a rental agreement
- Utility connection records confirmed occupancy
Outcome: Family provided with current city and approximate location. They successfully reestablished contact.
Case Study 3: Fraud Detection
An insurance company suspected a disability claimant was fraudulent. The claimant claimed complete inability to work due to back injury.
Investigation Process:
- Facebook profile showed privacy settings but had public friend list
- Friend profiles revealed tagged photos at recent sporting events
- Geo-tagged Instagram posts (from public friends) placed the claimant at a gym
- YouTube search found the claimant in background of a CrossFit competition video
- Timeline analysis showed athletic activity throughout the claimed disability period
Outcome: Claim denied; evidence forwarded to fraud investigation unit.
Building Your OSINT Practice: From Novice to Professional
Becoming proficient at OSINT requires deliberate practice. Here’s a development pathway:
Beginner Phase (Months 1-3)
Focus on fundamentals:
- Master Google advanced operators
- Set up and practice with 5-10 core tools
- Complete practice challenges (TraceLabs, OSINT exercises)
- Document your methodology for each investigation
- Join OSINT communities (Reddit’s r/OSINT, Twitter OSINT community)
Intermediate Phase (Months 4-9)
Develop specialization:
- Choose a focus area (corporate intelligence, cybersecurity, fraud investigation)
- Master tools specific to that domain
- Build custom tool sets and workflows
- Contribute to OSINT communities
- Take structured courses (SANS SEC497, Trace Labs certified training)
Advanced Phase (Months 10+)
Achieve professional competency:
- Develop proprietary techniques and tools
- Build automation for routine tasks
- Establish expertise in a niche area
- Consider certification (OSINT Certified Professional)
- Mentor others and share knowledge (maintaining OPSEC)
Common OSINT Mistakes (And How to Avoid Them)
Even experienced investigators make these errors:
Confirmation Bias
Seeking information that confirms preexisting theories while ignoring contradictory evidence. Combat this by actively seeking disconfirming information and maintaining multiple working hypotheses.
Source Reliability Failures
Treating all information as equally reliable. Social media claims require more verification than government records. Establish source hierarchies and demand appropriate verification levels.
OPSEC Neglect
Leaving traces of your investigation. Use VPNs, separate investigation accounts, and avoid direct platform interactions that alert targets. Investigators sometimes get caught because they accidentally like a target’s post or view a LinkedIn profile.
Scope Creep
Starting with a specific question and getting lost in tangential information. Maintain clear objectives and periodically reassess whether your current activity serves those goals.
Documentation Failures
Collecting information without recording where it came from. Six months later, you can’t verify findings or explain your methodology. Screenshot everything, record source URLs, and timestamp your collection.
The Future of OSINT: AI, Automation, and Evolution
OSINT continues evolving rapidly:
AI Integration
Tools like ChatGPT are already being integrated into OSINT workflows for data analysis, report generation, and pattern recognition. Expect AI-powered tools that automatically suggest investigation pathways and correlate data across sources.
Deepfake Detection
As synthetic media becomes more sophisticated, verifying authenticity becomes critical. New tools analyzing subtle artifacts in images, videos, and audio will become standard in OSINT toolkits.
Privacy Pushback
Increasing privacy regulations (GDPR, CCPA) and platform restrictions limit some traditional OSINT techniques. Successful investigators adapt by developing compliant methodologies and focusing on still-accessible sources.
Decentralized Data
Blockchain-based identity systems and decentralized social platforms will create new OSINT challenges and opportunities, requiring investigators to master new technologies and techniques.
Take Action: Start Your OSINT Journey
OSINT skills are increasingly valuable across industries—from corporate security to journalism, from fraud prevention to competitive intelligence. The techniques outlined here provide a foundation, but true expertise comes from consistent practice and continuous learning.
Ready to develop these skills systematically? Join the OSINT community:
Newsletter: https://coondivido.substack.com/
Telegram: https://t.me/osintaipertutti | https://t.me/osintprojectgroup
Start with simple exercises: pick a public figure and see how much you can learn using only publicly available information. Document your process, note dead ends, and refine your approach. Within weeks, you’ll be uncovering information you never knew was accessible.
The digital age has made privacy increasingly difficult—but it’s also democratized intelligence gathering. These same techniques protect you by revealing your own digital footprint. Master OSINT, and you’ll never look at online information the same way again.



