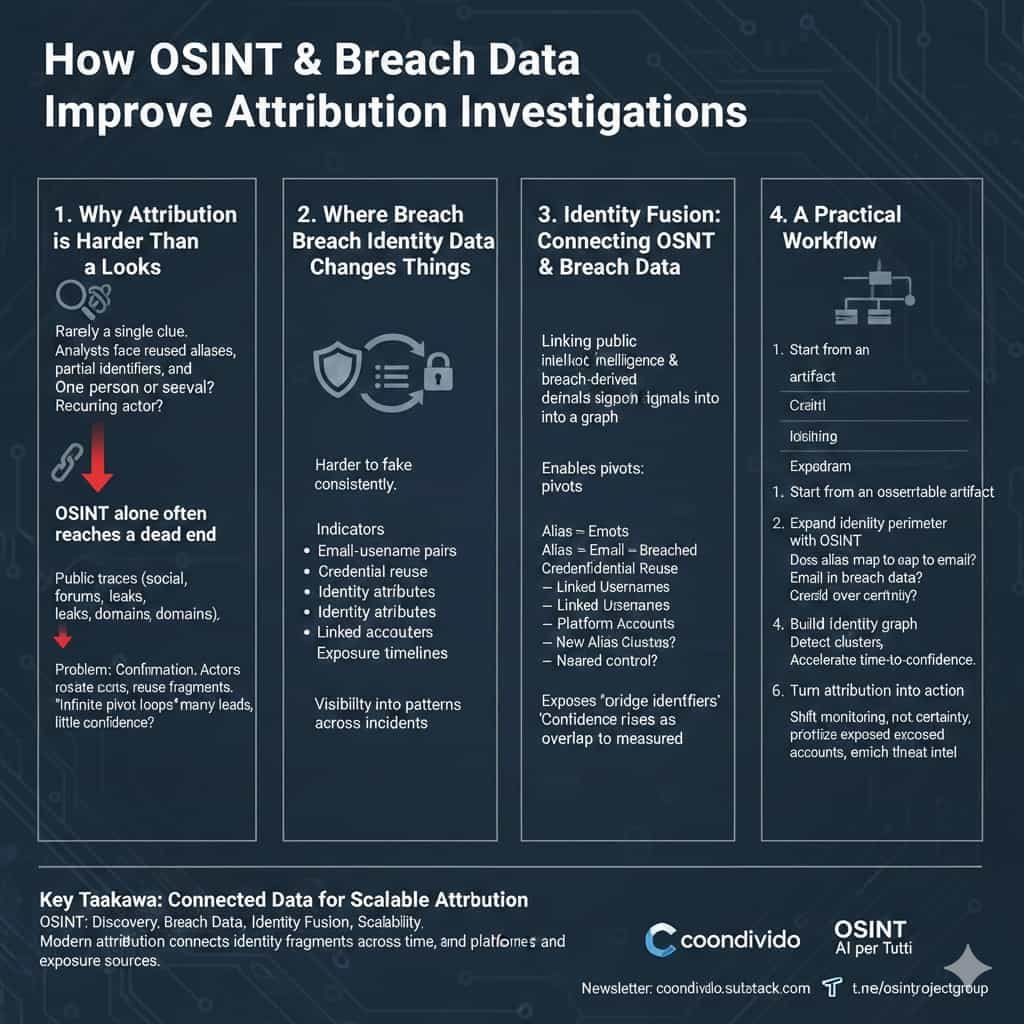
Why attribution is harder than it looks
Attribution rarely hinges on a single clue.
Most investigations stall in the middle, where analysts face reused aliases, partial identifiers, and signals that contradict each other.
A suspicious email address, a forum username, or a dark-web mention often raises the same questions:
Who is really behind this activity?
Do these identifiers belong to one person or several?
Is this a recurring actor or a one-off identity?
The document makes one point clear: attribution improves when OSINT is combined with verified breach identity data, not when it works alone. How OSINT + Breach Data Improve…
Why OSINT alone often reaches a dead end
OSINT surfaces a wide range of public traces.
Social profiles, forum posts, leaked mentions, repositories, domains, messaging accounts.
The problem is not visibility.
The problem is confirmation.
Public traces rarely prove that two identifiers belong to the same operator. Threat actors rely on this gap. They rotate accounts, reuse fragments of past personas, and spread activity across platforms to blur identity boundaries.
This creates what the paper calls “infinite pivot loops”: many leads, little confidence. How OSINT + Breach Data Improve…
Where breach identity data changes the investigation
Breach identity data introduces signals that are harder to fake consistently over time.
According to the document, useful indicators include:
Email–username pairings
Credential reuse patterns
Identity attributes recurring across sources
Clusters of linked accounts
Exposure timelines
These elements do not replace OSINT.
They validate it.
Instead of relying on what an actor chooses to show publicly, investigators gain visibility into patterns that persist across incidents and datasets. How OSINT + Breach Data Improve…
Identity fusion: connecting OSINT and breach data
The real shift happens when OSINT and breach data stop being treated as separate workflows.
The paper describes this as identity fusion: linking public intelligence and breach-derived identity signals into a single graph.
This enables pivots such as:
Alias → email → breached credential reuse → linked usernames → platform accounts → new alias clusters
Graph-based analysis exposes “bridge identifiers” that connect personas previously treated as unrelated.
Coincidences become easier to discard.
Confidence rises because overlap is measured, not assumed. How OSINT + Breach Data Improve…
A practical workflow for attribution investigations
The document outlines a repeatable process used by security teams. Reframed here as a step-by-step guide.
1. Start from an observable artifact
This could be a dark-web reference, a phishing email, a leaked credential set, or a known alias.
Attribution always begins with something concrete.
2. Expand the identity perimeter with OSINT
Map everything publicly associated with that identifier.
Aliases, related handles, exposed emails, infrastructure traces, posting timelines, language patterns.
At this stage, quantity matters more than certainty.
3. Strengthen pivots using breach identity data
This is where weak links become meaningful.
The key questions shift from “does this look similar?” to:
Does this alias map to the same email across sources?
Does that email recur in verified breach datasets?
Are credentials reused across multiple accounts?
Do patterns suggest shared control?
These checks reduce guesswork. How OSINT + Breach Data Improve…
4. Build the identity graph
By correlating identifiers, investigators can detect clusters rather than isolated accounts.
This helps separate genuine connections from noise and accelerates time-to-confidence.
5. Score confidence, not certainty
The document is explicit: attribution is rarely absolute.
Confidence grows through low-probability overlaps, repeated reuse over time, and corroboration across sources.
The goal is a defensible assessment, not a perfect one.
6. Turn attribution into action
Once identity linkages are established, investigations should change behavior.
Monitoring priorities shift.
Exposed accounts receive attention.
Threat intelligence becomes richer for future cases. How OSINT + Breach Data Improve…
What security teams gain from this approach
When OSINT and breach identity intelligence work together, the paper highlights clear outcomes:
Faster investigations
Fewer false links
Stronger identity clustering
More actionable reporting
Reduced analyst fatigue
The advantage does not come from more data.
It comes from connected data. How OSINT + Breach Data Improve…
The key takeaway
OSINT excels at discovery.
Breach identity data strengthens validation.
Identity fusion makes attribution scalable.
Modern attribution is no longer driven by intuition alone.
It depends on connecting identity fragments across time, platforms, and exposure sources, then measuring how unlikely those overlaps really are. How OSINT + Breach Data Improve…
If your investigations keep circling the same aliases without reaching confidence, the issue may not be effort.
It may be missing links.




