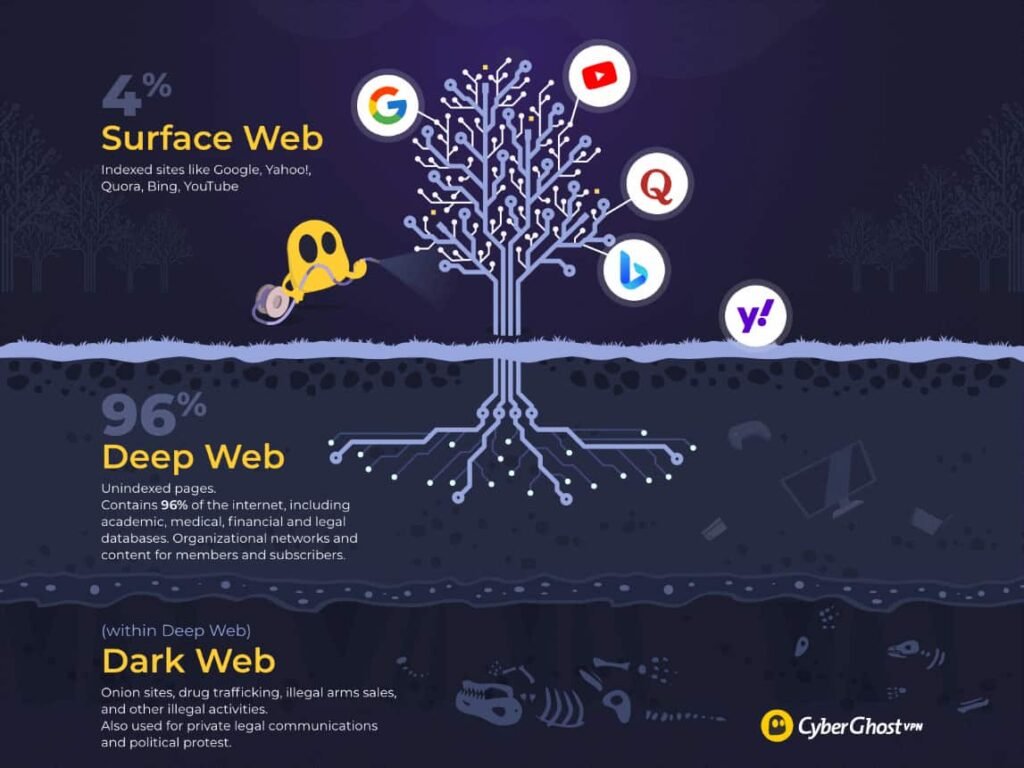
When we think about the “dark web,” most imagine glowing green text, Hollywood hackers, and underground conspiracies. The truth is less cinematic, but far more unsettling. Real attackers — and investigators — use a set of specialized OSINT (Open Source Intelligence) tools to map hidden services, trace digital footprints, and unearth data most people thought lost in the void.
This list isn’t about glorifying crime. It’s about awareness. These tools exist, they’re powerful, and understanding them is the first step in defending against them.
1. Dark Search – The Dark Web’s Google
Without a search engine, the dark web is like a library without a catalog. Dark Search indexes .onion sites across Tor, making hidden forums, marketplaces, and leaked databases findable. For researchers and threat actors alike, it’s the first stop: plug in a keyword, and Dark Search brings order to the chaos.
2. OnionScan – The X-ray of Hidden Services
This open-source scanner analyzes dark web sites for vulnerabilities: exposed IPs, outdated software, open ports, even images with metadata that reveal clues. Investigators and law enforcement use OnionScan to deanonymize criminals. For those trying to stay hidden, one misstep and OnionScan will expose it.
3. Ahmia – The Safer Search Alternative
Unlike Dark Search, Ahmia filters out abusive content, making it a cleaner entry point for journalists or academics. It indexes public-facing onion sites and provides insight into conversations on forums, blogs, and whistleblowing platforms. Ahmia listens where others only look.
4. Recon – The Swiss Army Knife
A modular reconnaissance framework that automates the collection of emails, IPs, breach data, and more. Hackers use Recon to map digital footprints, while investigators rely on its extensibility to keep pace with new data sources.
5. Maltego – Turning Data Into Patterns
Maltego transforms scattered information into dynamic graphs. Starting with an email or username, it reveals linked profiles, domains, and networks. For law enforcement, it’s indispensable for mapping disinformation campaigns or tracing online aliases to real-world identities.
6. SpiderFoot – Automation at Scale
Feed SpiderFoot a target domain, email, or username, and it queries hundreds of sources — from DNS records to dark web dumps — creating a dossier automatically. For security analysts, it’s like having a digital research team working in the background.
7. Hunchly – The Digital Notebook
Evidence on the dark web disappears fast. Hunchly, a browser add-on, automatically saves timestamped, verifiable records of every page you visit. Each file is hashed for authenticity, creating a forensic trail essential for law enforcement or corporate investigations.
8. Lampyre – Big Data for Threat Intel
Lampyre is built for heavy lifting. It processes huge datasets — emails, usernames, Bitcoin wallets — and connects them with malware IPs, hacker groups, and darknet forums. Think of it as a fusion of Maltego’s visualization with SpiderFoot’s automation, tuned for large-scale intelligence.
9. Tails – The Operating System of Anonymity
Tails is a live OS that routes all traffic through Tor and leaves no trace once shut down. It’s bundled with encryption tools, Tor Browser, and secure messaging apps. For journalists, whistleblowers, and yes, hackers, Tails is the cloak that makes everything else possible.
10. Creepy – The Geolocation Aggregator
Despite the name, Creepy does exactly what it promises: it scrapes geotags from social media posts and plots them on a map. Investigators can reconstruct movements, identify routines, and connect online identities to real-world locations. It’s where the digital world meets the physical.
Why This Matters
These ten tools form the hacker’s arsenal — but also the investigator’s. They highlight how much of our lives are traceable, how fragile anonymity can be, and how OSINT bridges the visible and invisible layers of the internet.
The takeaway is not to use them irresponsibly, but to understand the threat landscape they reveal. Because if you know how hackers see the world, you’re better prepared to defend against it.