🔐 Cybersecurity
Data Protection, Cybersecurity, and Corporate Privacy




cybersecurity
🛡️ Online Security
Cybersecurity, also known as digital security, includes all measures taken to protect information—such as accounts, files, and images—through strategies and defense actions for computers, mobile devices, servers, networks, and electronic systems, with the goal of preventing cyberattacks and data breaches.
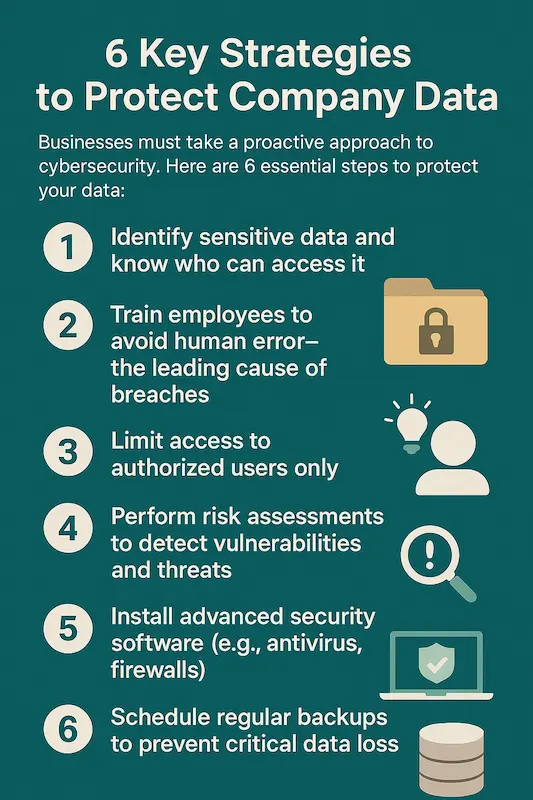
In recent years, the rise in cyber threats has made it clear: advanced security measures are essential to protect a company’s digital assets.
But what exactly does cybersecurity mean? What are its key features, and how can we protect our data?

The Most Powerful OSINT&AI Tools in One Place!
Discover our ever-growing collection of free tools for online research, data analysis, and AI-powered OSINT investigations.
Browse the Tool List 🔍cyber security
🔍 What Is Cybersecurity?
Cybersecurity, also known as IT security, refers to the technologies, strategies, and procedures used to protect data, networks, and information systems from unauthorized access, cyberattacks, and damage.
The main goals of cybersecurity are:
✅ Protect sensitive data from theft or tampering
✅ Ensure business and digital service continuity
✅ Prevent cyberattacks that could cause financial or reputational harm
✅ Ensure legal compliance, especially with regulations like GDPR


🚀 Want to explore the world of OSINT, Artificial Intelligence, and Cybersecurity but not sure where to begin?
Discover a selection of hands-on guides designed for students, self-learners, curious professionals, and tech enthusiasts.
📘 Start building practical, up-to-date skills today and navigate the web safely and confidently.
🛡️ Three Core Principles of Cybersecurity (CIA Triad)
Every cybersecurity strategy is built on three fundamental principles:

1️⃣ Availability: Ensuring Access to Data
Availability ensures that information is accessible to authorized users whenever needed.
🔷 Why is it important?
Maintains business continuity
Prevents service interruptions and ensures a smooth user experience
Reduces productivity loss caused by system or data downtime
🔧 How to ensure it?
✔ Regular backups to prevent data loss
✔ Redundant systems to avoid outages from hardware failures
✔ Disaster recovery plans to restore data in emergencies

2️⃣ Integrity: Ensuring Data Accuracy
Integrity ensures that data is not altered, corrupted, or deleted without authorization.
🔷 Why is it important?
Supports accurate and reliable decision-making
Prevents data manipulation and fraud
Avoids legal penalties due to non-compliance (e.g., GDPR)
🔧 How to ensure it?
✔ Hashing techniques to verify file integrity
✔ Version control to track changes
✔ Regular backups to recover original data if corruption occurs

3️⃣ Confidentiality: Protecting Sensitive Information
Confidentiality ensures that only authorized individuals can access sensitive information.
🔷 Why is it important?
Safeguards the privacy of individuals and organizations
Prevents leaks of confidential data that could harm reputation
Reduces the risk of financial fraud and identity theft
🔧 How to ensure it?
✔ Encryption to make data unreadable without authorization
✔ Multi-factor authentication (MFA) for secure access
✔ Role-based access control and permission management

🔍 DISCOVER THE WORLD OF OPEN SOURCE INTELLIGENCE!
Access top strategies, advanced tools, and proven methods to collect and analyze open-source data effectively and securely.